Security firm Acronis reports that a number of purported indie games use social engineering and stolen branding assets to trick people into installing malware.
The Acronis Threat Research Unit (TRU) uncovered a new malware campaign involving Leet Stealer, RMC Stealer (a modified version of Leet Stealer) and Sniffer Stealer. All of these stealer programs can steal your data.
The tricksters’ campaigns combine social engineering, gaming hype and stolen branding
assets to trick victims into installing malware disguised as indie game titles such as Baruda Quest, Warstorm Fire and Dire Talon.
The fake games are promoted through fraudulent websites and fake YouTube channels and are distributed mainly via Discord. Acronis leveraged the open-source tool urlscan.io to retrieve screenshots of fake websites that were no longer accessible at the time of the investigation.
Once installed, they deploy infostealers capable of harvesting browser data, credentials and Discord tokens.
The impact can be severe for the individual. Attackers may impersonate the victim to spread malware, scam others or even demand money in exchange for returning access (extortion). Sensitive data such as browser credentials, payment information, private messages and cryptowallets can also be compromised. Victims often face account loss, financial damage and emotional distress.
After analyzing multiple fake game samples, Acronis discovered that none of them contained any real game content. Instead, the malware relies on social engineering, leading victims to believe something went wrong during installation, or that their hardware simply doesn’t meet the game’s system requirements.
The report has a detailed technical breakdown of infostealers such as RMC Stealer. That data was accessible thanks to an operational mistake in which the attacker left the original, unobfuscated source code embedded in the malware package.
The background
As malware threats continue to evolve, a notable trend has emerged: a growing number of malicious programs are being distributed through Discord, particularly those built using the Electron framework.
Discord has a free base platform. It’s a cross-platform communication platform popular among gamers, developers, communities and friend groups. It supports voice, video
and text chat, and is widely used for sharing content in real time.
The Electron framework, while lesser-known outside of development circles, is an open-source tool that enables developers to build cross-platform desktop applications using JavaScript, HTML and CSS.
Electron combines Node.js for backend functionality and Chromium for rendering the UI. It’s the foundation behind many widely used applications, including Visual Studio Code, Spotify, Slack, Discord and certain versions of Skype and Microsoft Teams.
Acronis found recent stealer campaigns built on top of the Electron framework, highlighting the techniques and distribution methods it has observed.
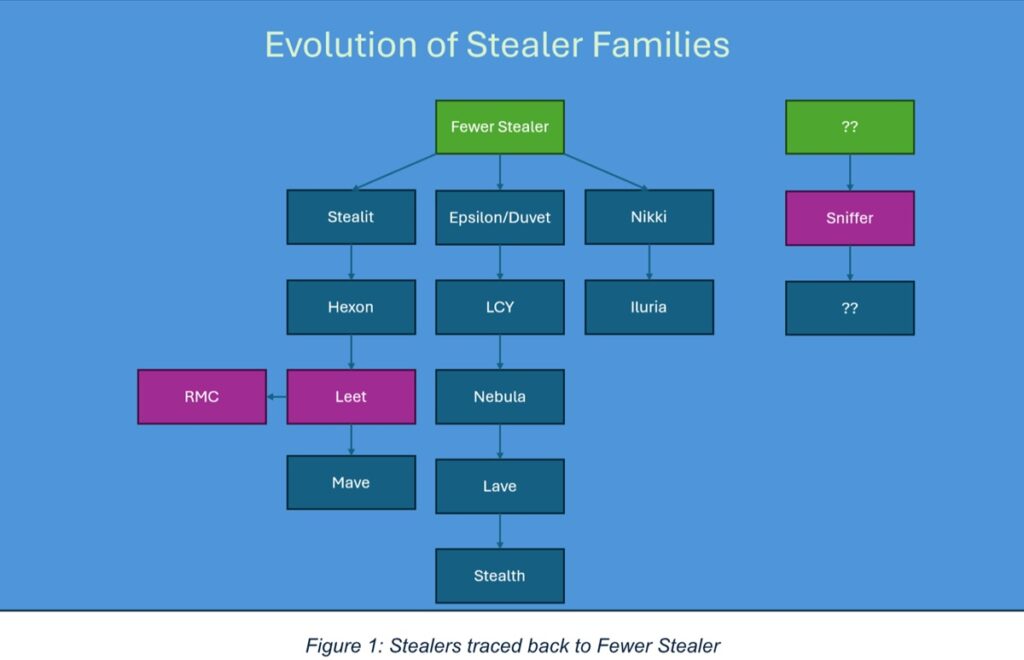
Acronis looked at examples involving Leet Stealer, RMC Stealer (a modified version of Leet Stealer) and Sniffer Stealer. The company’s investigation indicates that many Electron-based stealers can trace their roots back to Fewer Stealer, which appears to be a foundational tool in this malware family.
Games like Catly, Eden and Rooted are listed on Steam, but their release dates haven’t been announced yet. Some of them might eventually be available through Steam’s Early Access program, where players can try games before they’re officially finished. Because of this, the idea of a “beta installer” sounds believable and exciting to many gamers, especially those who enjoy finding new indie games.
Cybercriminals take advantage of this by creating fake game installers that actually contain malware, and they spread them on platforms like Discord where game links are often shared. The following sections present a selection of fake game examples observed over the past two months.
To make these fake games seem more convincing, the attackers often go the extra mile by creating dedicated websites and even YouTube channels to promote them. A prime example of this is Baruda Quest, the first fake game analyzed.

Fake YouTube channel: hxxps://www[.]youtube[.]com/watch?v=N3OTRiidWUQ
The website offered download links for Windows, Android and macOS. However, only the Windows version contained malware, an RMC Stealer variant. The other two links redirected users to the legitimate virtual world game Club Cooee, from which the attackers had stolen artwork and branding to make Baruda Quest appear authentic.
Fake game #2: Warstorm Fire
The Warstorm Fire website had its default language set to Portuguese, suggesting a likely origin in Brazil. The game’s visuals and branding were directly copied from the legitimate game Crossfire: Sierra Squad.
Fake game #3: Dire Talon
For this case, the attackers took the original game Project Feline and rebranded it as
their own, under the name Dire Talon.
Fake game #4: WarHeirs
Another rebranded game. Original is called The Braves.
For several of the fake webpages, the default language is set to Portuguese, which
aligns with what we observed in VirusTotal submission telemetry. The highest number of
samples (33%) came from Brazil, but the United States (30%) followed closely behind, suggesting the campaign may have expanded quickly across language and regional boundaries. Türkiye accounted for 17%, Germany was 7% and Saudi Arabia was 2%.
While the Portuguese language suggests the campaign may have originated in Brazil,
the strong presence of submissions from the U.S. shows that the malware has likely
been distributed more broadly, possibly through global platforms like Discord.
Conclusion
Stealers disguised as fake games and setup files demonstrate how modern malware campaigns have evolved beyond just technical tricks. They now rely heavily on social engineering, branding, and psychological cues to fool users. By disguising malware as games and backing it with fake websites and promotional materials, attackers blur the
line between legitimate content and deception.
Social media platforms such as Discord are popular among younger, tech-savvy audiences, and they serve as effective distribution channels, especially when attackers
leverage recognizable game names or early access hype.