Computer hacking saturates many mainstream releases including Mass Effect and Bioshock. If a game takes place in a futuristic or steampunk setting, then chances are that it's going to feature some sort of mini-game to access or bypass certain systems. It’s not the worst idea in the world, as hacking has fascinating gameplay implications and can help enhance a game world. However, developers drop the ball when it comes to actually executing a visual representation of these actions when they choose instead to utilize a random mini-game that has nothing to do with actual computer hacking. In an age where extensive research usually precedes production, developers have no real excuse for this.
Hacking started appearing as a game mechanic in old pen-and-paper RPGs, when dice rolls, skill levels, and difficulty ratings determined success. The actual process existed only in the player's imagination. This abstraction continued in early video games until designers decided to give players a tangible way of breaking into a computer or device.
 On the surface, this seemed like a good idea. It increased the gameplay variety for the player and made the game world more immersive. However, simulating actual hacking is difficult to accomplish in small bursts. This is where the hacking mini-game phenomenon started.
On the surface, this seemed like a good idea. It increased the gameplay variety for the player and made the game world more immersive. However, simulating actual hacking is difficult to accomplish in small bursts. This is where the hacking mini-game phenomenon started.
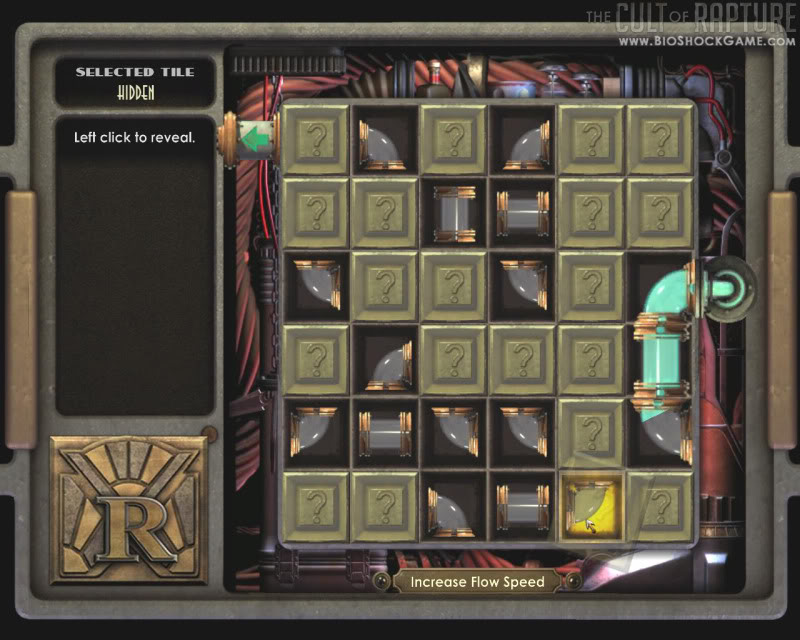
System Shock 2 and Bioshock both tried to accomplish this while remaining consistent with their worlds, though what you end up doing is still a far cry from actual hacking. System Shock 2’s method of manipulating square nodes is at least in line with what people imagine the process to be. Though Bioshock’s Pipe Mania clone mini-game is completely in line with the game’s steampunk setting, you’d be hard pressed to rationalize how getting goo from one end to another falls in line with what we know as hacking.
Worse still is where the developers don’t even try to make it consistent with its own world, like Mass Effect’s infamous Simon mini-game. How do you explain repeating a sound pattern as a means of gaining access to a sophisticated computer?
The problem with games that try to incorporate it is that developers put very little thought into making hacking work in the confines of a larger game. Of course, the reality of hacking might just be too mundane for modern audiences. It tends to involve lots and lots of text.
Remember working with MS-DOS back in the day? That’s in the ballpark of what you’d be seeing in a real-world hack. It’s about finding back doors into protected files and changing values to create vulnerabilities. Even something as simple as looking in the source code of a web page is a regular occurrence.
Given the fact that most actual hacking is all letters and numbers on a screen, it’s almost understandable why developers would want to fake more tangible, simplified, and graphically represented gameplay. After all, text adventures became nearly obsolete once graphical adventure games gained popularity. But you can find a satisfying amount of depth and cleverness under the surface that would do so much to enrich games if developers could replicate that feeling into a simplified and compact form.

This is why Uplink, Introversion’s debut game, is so impressive. It takes the concept of real computer hacking and builds a game around it. The interface completely commits by mimicking the all-text environment that hackers would use, with nothing else but a map for choosing workstations. The gameplay itself actually resembles an RPG where you take on jobs to delete, steal, or change data from workstations at corporations or universities.
It’s strangely compelling in its devotion to its inspiration, but it doesn’t fall into the trap of trying to replicate it exactly. Instead of arcane actions that regular players wouldn’t understand, the game provides players with tools that automate these actions, such as password crackers. However, a lot of authentic concepts still appear in the game, like IP addresses, traces, and accessing computers by bouncing a connection through many workstations to mask your address. It isn’t completely authentic or realistic, especially given the fact that one of the security options you can choose for your workstation is a self-destruct mechanism, but it’s quite possibly the closest a video game has gotten to doing hacking justice.
No one expects developers to copy real-world hacking exactly. They don’t even need to relate it to existing jargon. But don’t insult the player by trying to pass off Pipe Mania or Simon as a hack, because the things that make the art of hacking so engrossing and fun are then lost completely.