A sprawling malware cyber campaign is turning gamers’ hunger to gain an edge into a massive payday for threat actors, who are leveraging over 250 malware samples to steal
credentials and cryptocurrencies, according to research by CyberArk Labs.
The operation has already netted wallets containing over $135,000, according to a post by malware researcher Ari Novick. CyberArk Labs looked into a specific infection instance, exploring its mechanisms and sharing indicators of compromise (IoCs).
It’s no surprise that cheating is an attraction for possible malware attacks. Gamers tend to cheat so much in multiplayer games that developers spend a huge amount of attention on developing tools for protecting games like Call of Duty.
The StealC group is a Malware-as-a-Service (MaaS) group that provides access to their infostealer malware for various periods of time at varying prices. From what CyberArk observed, most of the StealC group’s customers buy access for a month and only create a small handful of samples.
In contrast, the threat actors from this campaign seem to have purchased longer access of at least three months. Additionally, CyberAkr observed significantly more builds being created in this campaign compared to others.
Not everything they do is unusual, though – like other threat actors, they are targeting
gamers, and more specifically, gamers who cheat.
Another unusual thing about this campaign is the use of StealC’s loader capabilities. StealC can be configured to double as a loader-type malware and download secondary payloads from a C2 server (doesn’t have to be the same as the first server). Once again, it appears that not many threat actors use this feature.
Still, the ones running the current campaign do use the loader capability to download what appears to be a custom lightweight CryptoJacker meant to steal cryptocurrencies from users on infected machines.
Infection chain
As stated, there seem to be multiple infection chains targeting gamers in this campaign.
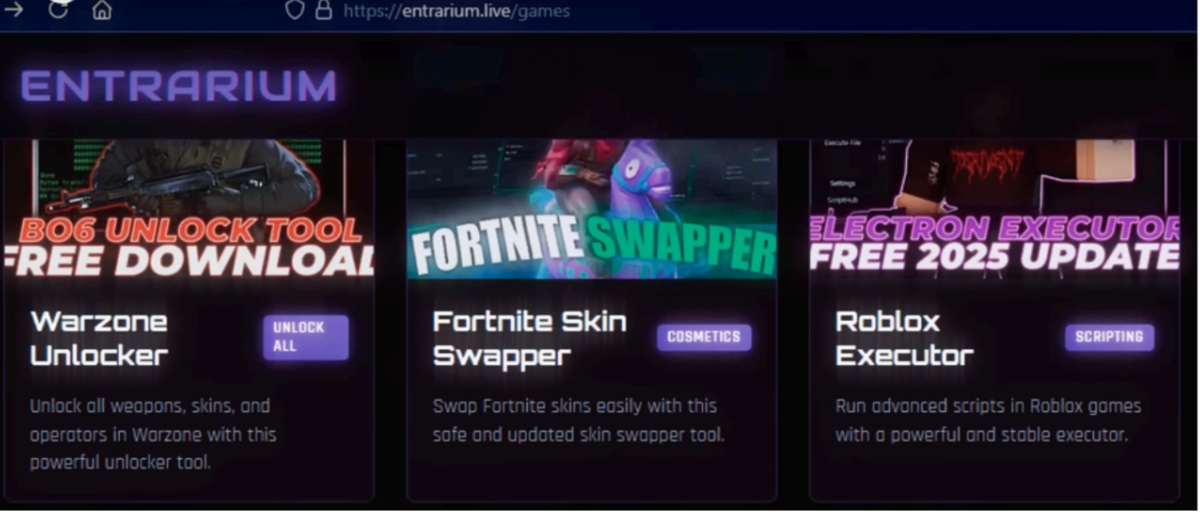
Previous reports have linked the website entrarium[.]live to malware distribution, and it
appears to serve as one of the starting points in this campaign as well. The Entrarium
site seems to promote various tools for modding and hacking different games, but it
appears that, in at least some of the cases, it has been used as a malware distribution vector.
Trying to download one of these tools redirects one to mega[.]nz, a file sharing
service that has been widely used by threat actors in previous malware distribution
campaigns. Once on mega[.]nz, the victims have to manually download an archive called
entrarium.zip containing the malware.
The threat actors don’t use too many addresses, but they seem to have a decent success rate.
As of August 19, 2025, the wallets held around a value of $139,405 (not quite as
much as MassJacker but significant nonetheless). However, it should be noted that CyberArk couldn’t access all the wallets, so the amount may be more.
In summary, this threat actor first caught CyberArk’s attention because of the large number of samples tied to a single C2, which also lasted an unusual amount of time. From there, just looking around on VirusTotal led to a lot of interesting stuff. Still, not everything here is new. Targeting gamers and, more specifically, those that cheat is a common practice of threat actors. It’s just like the old saying goes: Cheaters never win, and winners never cheat, CyberArk said.